Video Conferencing Showdown, Part 4 - Cisco Webex
Chelsea Sauder • May 22, 2020
In Part 4 of our Video Conferencing Showdown blog series, we’ll examine Cisco Webex Meetings. We’ll delve into privacy, vulnerabilities, encryption, and user settings. Make sure to check out our other posts in this Video Conferencing Showdown series: Part 1: Zoom, Part 2: Microsoft Teams, and Part 3: Google Meet.
WebEx (capital E) was founded in Silicon Valley in 1995. The company was purchased by Cisco Systems in 2007, and rebranded as “Webex” in 2018. One of the founders of WebEx went on to be an early investor and is an advisor for Zoom; the founder of Zoom was a former engineer and executive before and after the Cisco acquisition as well.
Cisco has reported they had three times the number of meeting minutes
in April as compared to January 2020.
Privacy
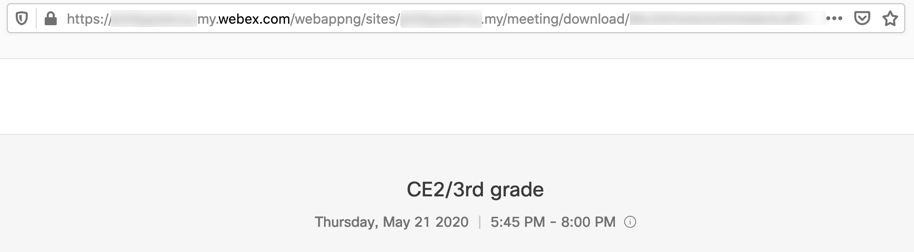
Webex Meetings URLs usually have the following two formats. The first is a regular, scheduled meeting; the second is an individual’s Personal Meeting Room, generally used for on-demand instant meetings where collaboration or screen sharing is quickly desired.
- companyname.webex.com/company/j.php?MTID=meetingid
- companyname.[my]webex.com/join/firstname.lastname
It’s certainly not hard to guess the Personal Meeting Room if you know the company and person, and what this means for the scheduled meetings is that the meeting IDs can be harvested, chiefly by two ways:
- People aren’t diligent about protecting them, such as a screen shot of a Webex meeting where the URL is visible
- The meeting URL makes its way into an online database, such as when it’s detected by a security filter of some kind
While writing this, a search of an online threat database used in the security industry yielded approximately 4,100 meeting URLs and 250 Personal Meeting Rooms in about 32 seconds.
The information is out there, and it’s not difficult to come by. But everybody’s heard about Zoombombing, there can’t possibly be any meetings in there that could let us just join, right?
“Oh, d-dear. I guess I haven’t gotten all the bugs out of my magic yet.”
– Piglet, “Owl Feathers”, 14-Jan-1989
Cisco publishes a Privacy Data Sheet covering Webex meetings which describes the processing of personal data or PII. Data is collected from meeting hosts and participants and includes:
- Name
- Email Address
- Public IP Address
- IP Addresses Along the Network Path
- Web browser information
- MAC Address of Your Client (as applicable)
- Actions Taken
- Geographic region
- Meeting Session Information (title, data and time, frequency, average and actual duration, quantity, quality, network activity, and network connectivity)
One particular interesting bit I liked seeing is that Cisco makes it clear that if you’re using a Webex Meetings account at work, the data is accessible to your employer, who may have their own policies concerning use, monitoring, and retention of the data. In the same vein, if you participate in a meeting hosted by another organization, the Webex Meetings data is thus under their data policies.
Vulnerabilities
One new threat to Webex Meetings users isn’t a vulnerability present in Webex itself at all. According to email security company Abnormal Security, between 2,800 and 5,000 mailboxes have received phishing emails after their usernames and passwords. The email steals graphics and formatting from legitimate Cisco emails and closely resembles the automated SSL certificate error alerts
that Cisco does send out. The login link goes not to Webex, however, but at the domain “app-login-webex.com” – additionally, the app-login-webex.com link is wrapped in a SendGrid link for concealment.
If you thought the Webex-bombing example above was bad, it’s only recently that Webex meeting passwords actually work in all cases. A vulnerability called CVE-2020-3142
which Cisco discovered in late January 2020 allowed unauthorized parties to join a Webex
meeting from an iOS or Android device even when password protection was in use. Cisco has fixed the problem on the platform side – no user action is required.
This comes after a group of high severity vulnerabilities (CVE-2019-1771, CVE-2019-1772, CVE-2019-1773) in May 2019 allowing remote code execution attacks in Webex software for Windows.
Encryption
In the Privacy Data Sheet, Cisco attests that currently, all personal data is encrypted in transit, and some at rest. In a technical whitepaper about Webex security, Cisco says that all Webex Meetings media streams – audio, video, VoIP, screen share, and document share – are encrypted between you and Webex Cloud. Webex Cloud service then re-encrypts the media stream before sending it to other users. A possible exception to this is if your company as a Webex customer enable joining your meetings using third-party video end points – in this case those attendees may be sending your meeting data across the Internet unencrypted.
Typically, the UDP protocol is used for media stream transmission and it is encrypted using AES-128. A block cipher mode is not specified.
Like other providers, the media streams are decrypted by Webex Cloud (inside Cisco’s firewalls) so the service itself can record the meetings. For businesses that want or require it, Cisco optionally provides true end-to-end encryption where the media streams are not decrypted in Webex Cloud, but this comes at a cost. It removes these Webex Meetings features:
- Ability to use the Web App instead of the desktop client;
- Cloud based meeting recording;
- Join Before Host
- Video Endpoints
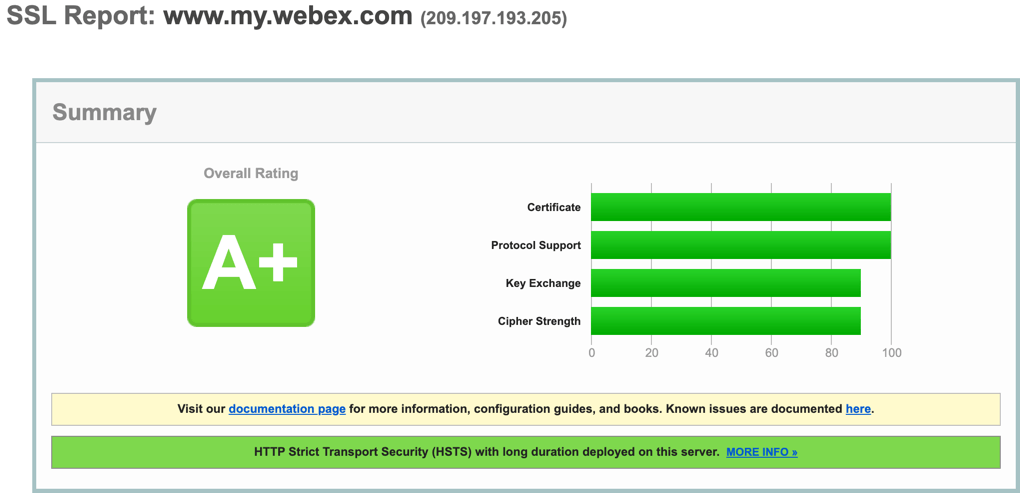
SSL Labs gives Webex Meetings URLs *.my.webex.com an A+ rating. Note that these sites do not support anything lower than TLS 1.2, so Cisco is a little ahead of the rest regarding deprecation of TLS 1.1 and 1.0 support.
User Settings
Let's Talk
Cisco publishes several Webex Best Practices for Secure Meetings guides.
Hosts
suggests that the meeting host observe the following:
- Do not share your Audio PIN with anyone
- Provide meeting passwords only to users who need them
- Never share sensitive information in your meeting until you are certain who is in attendance
- Effective use and controls of your Personal Room – enable automatic locking of the room when your meeting starts
- Meeting Scheduling – use complex passwords and exclude it from email invitation; request that invitees do not forward invitations
- During the Meeting – once all expected attendees are present, you may lock the meeting against further attendees joining. Be aware that if someone disconnects inadvertently you will need to unlock the meeting before they can re-join
- After the Meeting – If recordings are created, you assign a password to them before sharing the files. Delete recordings which are no longer needed
Site Administration
suggests that Webex administrators within an organization observe these practices:
- Make all meetings unlisted
- Require passwords for all meetings
- Enforce meeting password when joining from phone or video conferencing system
- Require sign in – however, only works if you never have attendees external to your company/Webex site
- Disallow Join Before Host
- Enforce Personal Room Locking
- Restrict Unauthenticated/Anonymous users
- Account Security – lock out accounts after a number of failed login attempts, set a password policy
Summary
Cisco Webex Meetings is one of the oldest collaboration platforms out there, and it’s good at what it does. Cisco has good security and privacy policies, but even they aren’t immune to software vulnerabilities and unwanted meeting intrusion; most of the Webexbombing can be avoided with host choices and user settings. Webex Meetings is a good choice for personal use as their free plan has been bumped up to a max of 100 participants and from 40 minutes duration to unlimited.
Come back next week for the wrap-up episode of our Video Conferencing Showdown!
Share this post with others:
When it comes to automating processes around your business, it can simultaneously seem like everything can be automated, and absolutely nothing can be automated. As with many other things, the real answer is somewhere in the middle but can be a bit challenging to put your finger on. These projects usually start when someone at the strategic level of the organization has decreed that “we are going to automate!” and either they personally go on the hunt for what to automate or they hand it off to someone on their team to go do the leg work and come back with “automation” (maybe in a nice box with a bow on it). Sound familiar?

Data is everywhere. You’ve got a lot to focus on and it can be hard to stay on top of what’s going on with your business. Report creation in Excel is often time-consuming and can quickly become a nightmare. Modernizing your reports and streamlining your process with PowerBI to get more reliable and consistent reporting across all of your systems can be a game changer for your business. Read on to learn about three key acceleration tactics that our team uses on every implementation that we facilitate.

83% of knowledge workers require technology to work together. Microsoft Teams is a cloud-based collaboration and communication tool that lets workers share the right information to the right people all through one integrated platform. According to a Forrester report, The Total Economic Impact of Microsoft Teams, there are a variety of ways using Teams saves organizations time and money. Read and download the infographic to share here .
How to Get Started with the Power Automate app for Teams You can get started with Power Automate app in just 3 quick steps: Click on the … in the left-hand corner of your teams browser Search for “Power Automate” Click on the Power Automate app icon and pin it to your left-hand Teams navigation panel
As mentioned, there are several options available for automating your business. One of our favorite low-code/no-code options is the Microsoft Power Platform. As a suite of 4 different tools, the Power Platform can automate routine tasks, customer support, data visualization, and more. A few highlights on the effectiveness of the Power Platform are:

It is no secret that 2020 and the coronavirus pandemic altered the reality of doing business. These changes are showing little signs of letting up and a lot of the adjustments made to respond to a remote workforce may very well become a permanent feature in daily business operations. As business decision makers (BDMs) and IT decision makers (ITDMs) head into a new year it is important to keep an eye out for technology solutions that can further support these operational changes while increasing efficiency. This post briefly highlights the top 3 digital solutions we have our eyes on for 2021 and our Microsoft-based clients.

In our latest video series, Patrick Boren, Principal Consultant at TexasPGB, introduces the newest addition to the Microsoft Project family, Microsoft Project Operations. In this video Patrick discusses: What challenges Project Operations aims to solve What is Project Operations and common use cases for the tool Who uses Project Operations Upcoming "Day in the Life" Sessions Watch the video or read the condensed transcript below.
Having a wealth of data at your fingertips is great, but what happens when your data is so vast that it takes you years to make a key discovery? A friend of mine told me a story recently about an experience he had. His first company conducted a VP meeting every quarter – everyone scrambling to put together their presentations and make their case based on the data from Excel spreadsheets. Departments and information tended to be segmented into silos. While much of the data could be shared across the company, rarely was it compiled in a way to show how one area of the business could affect another.

If you are looking to migrate your data to Microsoft 365 there are two common methods to funnel your data - SharePoint or Common Data Service (CDS). SharePoint solutions take advantage of lists and libraries. Data is housed, originated, and manipulated entirely within the SharePoint platform. CDS solutions use both standard and custom entities to collect and house data that is then integrated across the Microsoft 365 platform. Below we will review a few ways each method is different and what you should look for before making a final decision for your data migration plan.
When it comes to technology, do you have a one-size-fits-all vendor? In today’s world of cost cutting, we see more and more organizations that end up missing out on huge technology opportunities by assuming a single vendor can and will do it all. As a technology consulting firm, we’re frequently asked “aren’t you the same as my managed service provider (MSP)?” Fortunately, for those that ask, we’re able to shed light on how a Technology Consulting Firm varies from an MSP.