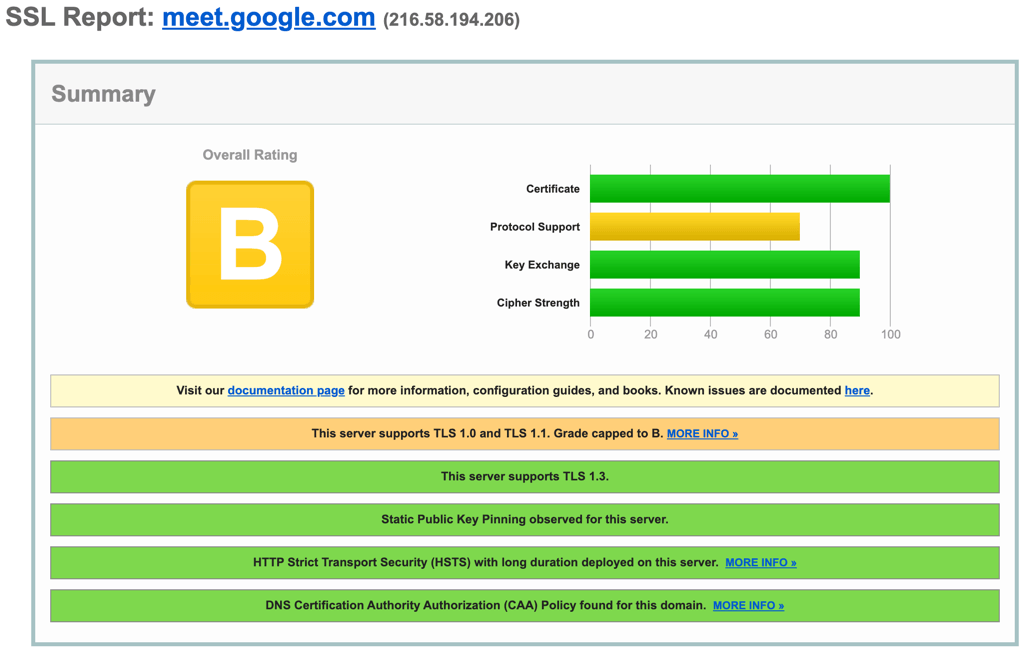
Video Conferencing Showdown, Part 3 - Google Meet
Chelsea Sauder • May 15, 2020
In Part 3 of our Video Conferencing Showdown blog series, we’ll examine Google Meet, the new name for Google Hangouts Meet. We’ll delve into privacy, vulnerabilities, encryption, and user settings. Make sure to check out our other posts in this Video Conferencing Showdown series: Part 1: Zoom
and Part 2: Microsoft Teams.
The latest features added to Google Meet are intended as a shot across the bow for Zoom. Google promised by the end of April that Meet would have the ability to view 16 participant windows at once. This makes large meetings much easier to deal with – and has been an optional Zoom layout for quite some time.
Similar to the Office 365 integration covered in our post with Microsoft Teams, many people already have access to Google Meet via their G Suite subscription. If your company uses Gmail for their corporate email, you’ve got access to Meet, and Google is working on a “join from email” integration with Gmail.
Google seems intent on seizing the current opportunity for videoconferencing use, telling Reuters they're adding 2 million users per day
as of April 9. That said, Meet until extremely recently was available only for schools, government, and business users. There’s a free equivalent called Google Hangouts (not the same thing as the previous name, Google Hangouts Meet)
Interestingly, Google VP Javier Soltero was quoted in that Reuters article criticizing competitors that not developing safeguards for free tools is “inherently wrong” -- but it’s very important to note that Google’s free Hangouts does not include security and meeting control features found in Meet. I believe this was foreshadowing, though, because on April 29, Soltero announced that Meet will be free for everyone. It’s a roll out several weeks long though, so you might not be able to get it just yet.
Privacy
In March, Google gave their educational users more control over who could join meetings, well before Zoom did similarly to curb Zoombombing. As it currently stands with Google Meet, only invited guests may join
a meeting, and only if they’re logged in. That means unlike Zoom, where meeting participants do not need to have their own Zoom account, you may only join a Meet instance if you’re signed into a Google Account. Google Accounts, especially when signed in via Google Chrome, do come with their own tracking and privacy concerns.
Meet umbrellas under the Google Cloud privacy and data protection
policies:
- Control over your data—Meet adheres to the same robust privacy commitments and data protections as the rest of Google Cloud’s enterprise services.
- Customers own their data, not Google.
- Google does not use customer data for advertising or sell customer data to third parties.
- Customer data is encrypted in transit and customer recordings stored in Google Drive are encrypted at rest by default.
- Meet does not have user attention-tracking features or software.
- You can set retention policies for Meet recordings with Google Vault to help fulfill legal obligations.
- Compliance—Our products, including Meet, regularly undergo independent verification of their security, privacy, and compliance controls. We consistently achieve certifications, attestations of compliance, or audit reports against global standards. We’ve also created resource documents and mappings against frameworks and laws where formal certifications or attestations might not be required or applied.
- Transparency—We follow a rigid process for responding to any government requests for customer data. We also disclose information about the number and type of requests we receive from governments through our Google Transparency Report.
Meet meeting codes are 10 characters
long and use 25 characters in the set. As a result, brute force guessing of a meeting ID isn’t practical. Additionally, there’s one more rather cool security check designed to thwart unwanted external guests, and it is that participants outside of your organization may directly join a video meeting only if they are
on the calendar invite, or specifically invited by a user from your company. Any other potential external attendee may request to join, but this request must be approved by someone within your company before they’re admitted. Finally, external users may join a meeting only up to 15 minutes prior to its scheduled start, so nobody’s allowed to loiter in your virtual conference room, waiting for something interesting to happen.
Google changed the world in 1998 with the commercial launch of the eponymous search engine, sporting the motto “don’t be evil,”
a phrase which was part of the corporate code of conduct since 2000. It was, however, removed from the document
in spring 2018, and Google isn’t known as the most privacy focused
tech company. Google pulls in an enormous amount of cash by aggregating and mining your online activities and personal information and using that data to display targeted ads. There’s also their history of abruptly killing off support of projects, several of which have been video conferencing and meeting apps.
REMEMBER - Google profits off selling data, not privacy
Vulnerabilities
Meet is usually run from entirely within a web browser
versus a standalone application such as with Zoom, Teams, or WebEx. To borrow a security industry term, this reduces the attack surface
of the application a great deal. There is a desktop application, first called Hangouts Chat, now called Google Chat, released in February 2018. It’s a Progressive Web Application (PWA) written in Electron
(developed and maintained by GitHub, now owned by Microsoft!) which mashes together the Chromium rendering engine (essentially a mini-browser) and Node.js JavaScript runtime environment. Based on the fact that Electron apps are just web apps running in the Chromium engine, they can be vulnerable to typical web attacks like cross-site scripting, and these (and other critical severity) vulnerabilities have been found in several Electron releases.
Yes, you can download and use it, but I wouldn’t suggest it:
- There’s no real advantage over running it natively in your web browser;
- Google asserts that no updating is required because the app automatically does it via the web, and it uses the Chromium engine which itself is updated in parallel with Google Chrome. That said, there’s no easy way to verify these, but what we do know: as of this writing, the version.electron file included in the MacOS distribution specifies Electron version 7.1.2 is in use. The current stable version is 8.2.5 – and even though 7.1.2 was only released on March 24, 2020, there’s a long list of applicable Electron vulnerabilities.
- A penetration tester and security researcher named Michał Bentkowski discovered in 2018 that open URL redirection in the Hangouts Chat app could be abused in a manner that might send people to phishing sites. Google patched this quickly, but it’s a problem endemic to the Electron framework.
These protocol versions are less secure and less preferred than TLS 1.2 and 1.3, however many Internet users still require their use – like anybody still using Internet Explorer v11 on Windows 7. That means there are still somewhere around 850,000 websites that use TLS 1.0 and 1.1. As mentioned in the Teams post, Microsoft plans to remove support for TLS 1.0 and 1.1 in June 2020. I wasn’t able to locate a similar definitive date for Google’s plans with older TLS versions.
Google boasts, and perhaps rightfully so, that Meet’s security controls are turned on by default. Important protection measures are just part of the service
and don’t require any intervention on the part of the users. As mentioned, users of the web browsers Google Chrome, Mozilla Firefox, Apple Safari, and Microsoft Edge (not IE!) don’t require any plugins or additional software. Mobile devices do require a client app, which is available from the device’s respective app store.
One setting we would recommend invoking is the use of multifactor authentication, such as a physical security key, a rolling code authenticator app like Google Authenticator, a two-step verification app like Google Prompt, or (least favorably; please don’t do this unless nothing else works) by SMS text message.
Lastly, it is possible for Meet users who are part of an organization using G Suite to eschew password authentication completely
in favor of single sign-on, or SSO. You can enforce MFA with SSO
but while this option is worth mentioning, it’s unfortunately not applicable to the individual user
because it requires a corporate identity provider set up for Meet and the rest of G Suite.
Summary
Overall, Google does a great job providing services which are robust, easy to use, and have good inherent security controls. It’s up to the individual how much they trust Google with their online activities, metadata, and various things Google tracks and monetizes. Similar to Microsoft Teams and Office 365, Meet is the logical choice if you’re already part of the G Suite at your company, and it is certainly exciting news that Google is releasing Meet for everyone this month, because its Hangouts predecessor was lacking for security and privacy controls. The same disclaimer (affectionately called “The Offspring clause”) from last week applies though – if your Google Meet account is provided by work, you should consider carefully if you want to use it for personal video conferences as well.
Come back next week (and each week in May) for another episode of Video Conferencing Showdown!
Connect with TexasPGB
Share this post with others:
When it comes to automating processes around your business, it can simultaneously seem like everything can be automated, and absolutely nothing can be automated. As with many other things, the real answer is somewhere in the middle but can be a bit challenging to put your finger on. These projects usually start when someone at the strategic level of the organization has decreed that “we are going to automate!” and either they personally go on the hunt for what to automate or they hand it off to someone on their team to go do the leg work and come back with “automation” (maybe in a nice box with a bow on it). Sound familiar?

Data is everywhere. You’ve got a lot to focus on and it can be hard to stay on top of what’s going on with your business. Report creation in Excel is often time-consuming and can quickly become a nightmare. Modernizing your reports and streamlining your process with PowerBI to get more reliable and consistent reporting across all of your systems can be a game changer for your business. Read on to learn about three key acceleration tactics that our team uses on every implementation that we facilitate.

83% of knowledge workers require technology to work together. Microsoft Teams is a cloud-based collaboration and communication tool that lets workers share the right information to the right people all through one integrated platform. According to a Forrester report, The Total Economic Impact of Microsoft Teams, there are a variety of ways using Teams saves organizations time and money. Read and download the infographic to share here .
How to Get Started with the Power Automate app for Teams You can get started with Power Automate app in just 3 quick steps: Click on the … in the left-hand corner of your teams browser Search for “Power Automate” Click on the Power Automate app icon and pin it to your left-hand Teams navigation panel
As mentioned, there are several options available for automating your business. One of our favorite low-code/no-code options is the Microsoft Power Platform. As a suite of 4 different tools, the Power Platform can automate routine tasks, customer support, data visualization, and more. A few highlights on the effectiveness of the Power Platform are:

It is no secret that 2020 and the coronavirus pandemic altered the reality of doing business. These changes are showing little signs of letting up and a lot of the adjustments made to respond to a remote workforce may very well become a permanent feature in daily business operations. As business decision makers (BDMs) and IT decision makers (ITDMs) head into a new year it is important to keep an eye out for technology solutions that can further support these operational changes while increasing efficiency. This post briefly highlights the top 3 digital solutions we have our eyes on for 2021 and our Microsoft-based clients.

In our latest video series, Patrick Boren, Principal Consultant at TexasPGB, introduces the newest addition to the Microsoft Project family, Microsoft Project Operations. In this video Patrick discusses: What challenges Project Operations aims to solve What is Project Operations and common use cases for the tool Who uses Project Operations Upcoming "Day in the Life" Sessions Watch the video or read the condensed transcript below.
Having a wealth of data at your fingertips is great, but what happens when your data is so vast that it takes you years to make a key discovery? A friend of mine told me a story recently about an experience he had. His first company conducted a VP meeting every quarter – everyone scrambling to put together their presentations and make their case based on the data from Excel spreadsheets. Departments and information tended to be segmented into silos. While much of the data could be shared across the company, rarely was it compiled in a way to show how one area of the business could affect another.

If you are looking to migrate your data to Microsoft 365 there are two common methods to funnel your data - SharePoint or Common Data Service (CDS). SharePoint solutions take advantage of lists and libraries. Data is housed, originated, and manipulated entirely within the SharePoint platform. CDS solutions use both standard and custom entities to collect and house data that is then integrated across the Microsoft 365 platform. Below we will review a few ways each method is different and what you should look for before making a final decision for your data migration plan.
When it comes to technology, do you have a one-size-fits-all vendor? In today’s world of cost cutting, we see more and more organizations that end up missing out on huge technology opportunities by assuming a single vendor can and will do it all. As a technology consulting firm, we’re frequently asked “aren’t you the same as my managed service provider (MSP)?” Fortunately, for those that ask, we’re able to shed light on how a Technology Consulting Firm varies from an MSP.