Anti-Phishing PowerShell Tutorial
Anti-Phishing PowerShell Tutorial
Recognizing phishing messages can be a real challenge.
One tool in the toolbox of many bad actors is to setup an email address with the same display name as someone in your organization, typically someone in leadership. Using that account, they send an email with an "urgent" need to someone, typically a front-line worker, who they hope will act on impulse and do what they've asked, rather than slow down and recognize the email was actually not from anyone on the management team.
One tool in the toolbox of many bad actors is to setup an email address with the same display name as someone in your organization, typically someone in leadership. Using that account, they send an email with an "urgent" need to someone, typically a front-line worker, who they hope will act on impulse and do what they've asked, rather than slow down and recognize the email was actually not from anyone on the management team.
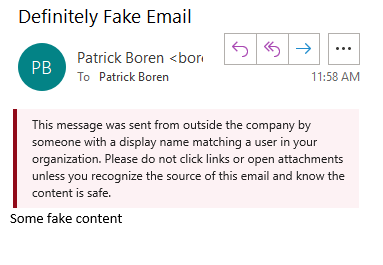
To protect your organization from this type of exploit, we recommend implementing an email rule that flags emails which come from an address outside of your organization but have a display name as someone within your organization.
Using the PowerShell scripts at the link below and following the video tutorial at the bottom of the page, you'll be able to implement the following notice for all users in your organization:
There are 2 versions of the PowerShell Script that we'll provide - one applies if you do NOT use multi-factor authentication in your Office 365 tenant, and one which applies if you DO use multi-factor authentication in your Office 365 Tenant.
For the PowerShell file for tenants WITHOUT multi-factor authentication, click here.
For the PowerShell file for tenants WITH multi-factor authentication, click here.
Tutorial for Office 365 Tenants
with Multi-factor Authentication
Tutorial for Office 365 Tenants
without
Multi-factor Authentication
Follow Us
TexasPGB is a digital solutions and technology consulting firm powering businesses through digital transformation, cloud services, and custom application development.
© 2025
All Rights Reserved | TexasPGB